CryptoDB
Dumbo, Jumbo, and Delirium: Parallel Authenticated Encryption for the Lightweight Circus
| Authors: |
|
|---|---|
| Download: | |
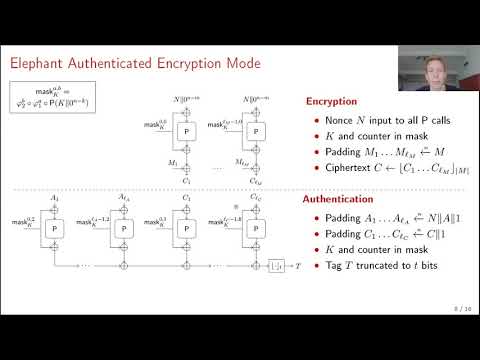
| Abstract: | With the trend to connect more and more devices to the Internet, authenticated encryption has become a major backbone in securing the communication, not only between these devices and servers, but also the direct communication among these devices. Most authenticated encryption algorithms used in practice are developed to perform well on modern high-end devices, but are not necessarily suited for usage on resource-constrained devices. We present a lightweight authenticated encryption scheme, called Elephant. Elephant retains the advantages of GCM such as parallelism, but is tailored to the needs of resource-constrained devices. The two smallest instances of Elephant, Dumbo and Jumbo, are based on the 160-bit and 176-bit Spongent permutation, respectively, and are particularly suited for hardware; the largest instance of Elephant, Delirium, is based on 200-bit Keccak and is developed towards software use. All three instances are parallelizable, have a small state size while achieving a high level of security, and are constant time by design. |
Video from TOSC 2020
BibTeX
@article{tosc-2020-30509,
title={Dumbo, Jumbo, and Delirium: Parallel Authenticated Encryption for the Lightweight Circus},
journal={IACR Transactions on Symmetric Cryptology},
publisher={Ruhr-Universität Bochum},
volume={2020, Special Issue 1},
pages={5-30},
url={https://tosc.iacr.org/index.php/ToSC/article/view/8616},
doi={10.13154/tosc.v2020.iS1.5-30},
author={Tim Beyne and Yu Long Chen and Christoph Dobraunig and Bart Mennink},
year=2020
}